[SC-100] Microsoft Graph Refresher
In case I'm not the only person who needed a refresher on Microsoft Graph, here are a few helpful links:
[SC-100] Identity is more than a username
While studying for the SC-100 exam, a concept really resonated with me: the definition of identity and its purpose in security.
I think for some folks (myself included), it's been all too easy to think of "identity" as a singular credential; a unique data element. Like an ID card. While understandable, I think that . . .
[SC-100] NIST 800-61 response management phases
I'm digging this simple (but functional!) illustration of the NIST 800-161 response management phases, courtesy of Microsoft Learning:
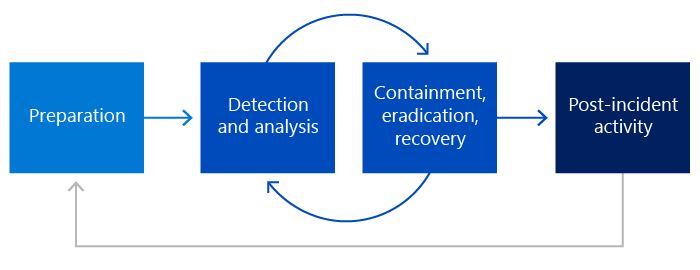
Good stuff!
[SC-100] Azure Monitor Agent vs Log Analytics Agent
I came across a nifty article explaining the difference between the legacy Log Analytics Agent and Azure Monitor Agent.
There's some feature improvements in terms of what logs can be retrieved with AMA but I think the biggest notable difference is performance-related. As per Microsoft: "The Azure Monitor agent provides a . . .
Cybersecurity and productivity
I came across a nifty quote by Pete Zerger while watching one of his LinkedIn Learning courses. This one really resonated with me:
Focus on security and productivity. Ensure that security enables productivity as well as reducing risk. If it hampers productivity or increases risk, reconsider.
I know at first . . .
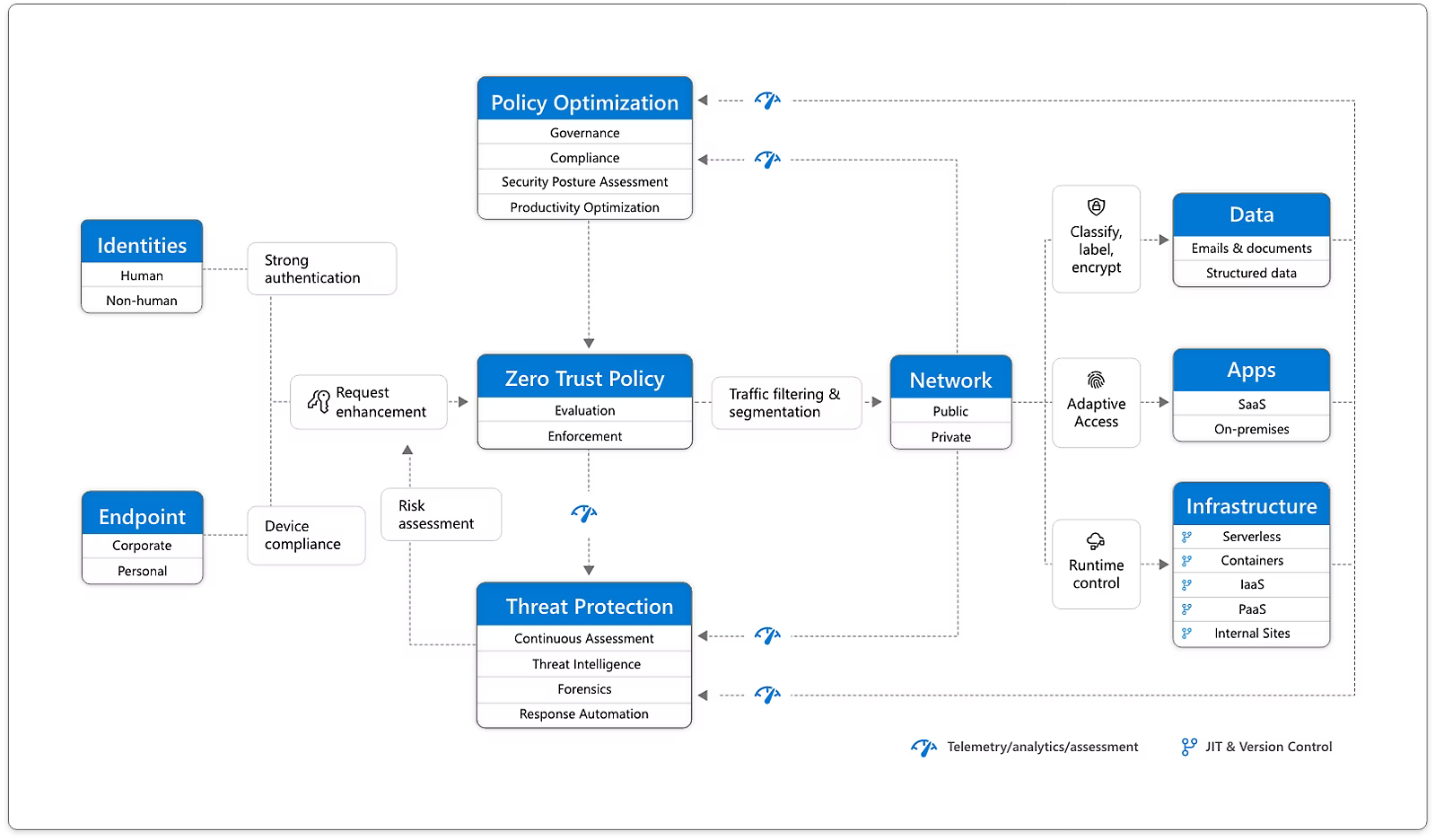
[SC-100 Exam Prep] Zero trust example workflow topology
A (zero trust) picture is worth a thousand words :-)
In preparing for the Microsoft SC-100 exam, I came across a nifty article from Microsoft regarding their position on Zero Trust.
Among other things, it includes a high-level example diagram of a topology combining a number of concepts.
Check it out: