Security Certification Roadmap
[SC-100] Conditional access "what if" tool
More security controls in the market need a feature like this.
I'm digging the "What If" tool in Azure Conditional Access component. The idea is simple: as you're building policies, you can throw various scenarios at the policy engine to understand what the heck it'll do.
This gives admins the opportunity to observe effects and perhaps test variations of authentication use . . .
[SC-100] Azure Blueprints vs Azure Landing Zone
This was another topic that was a little confusing: what's the difference between Azure Blueprints and Azure Landing Zone?
I came across various Microsoft documentation but it was still a little... vague.
Here's a nice table, provided courtesy of Google Bard:
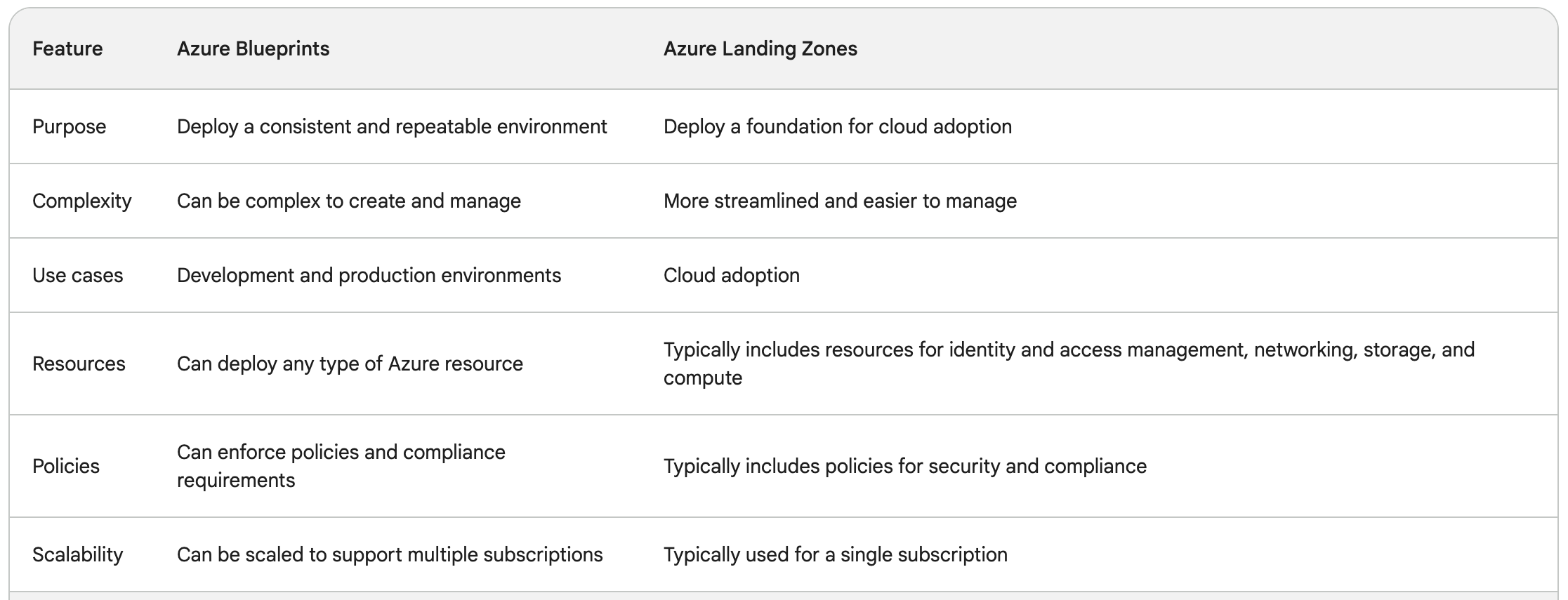
(usual disclaimer about AI-provided . . .
[SC-100] Defender for Cloud - Recommendations vs Alerts vs Vulnerability Assessment
Maybe it's just me, but I was starting to get a little confused on the differences in Azure workload security options. There's essentially three elements:
- "Security Recommendations"
- "Alerts"
- "Vulnerability Assessment"
What's the difference though? Just for the heck . . .
[SC-100] MCSB Compliance Control Overview
[SC-100] Conditional Access frameworks, policies, and naming conventions
OK, OK, so it may not necessarily be the most interesting topic...
Nevertheless, I think this article from Microsoft on Conditional Access framework and policies is an important one.
Of particular note, there's a section on naming conventions and how to develop/establish a system that scales well for designating . . .
[SC-100] Simplified explanation of technical response to incidents
While perusing a study guide for SC-100 exam, I came across a really nice and succinct explanation for technical response. It's one of my favorite quotes now:
(...) there are two key goals that every incident response should aim to address from a technical perspective. The first is identifying the scope of the attack (...) . . .
