Microsoft Storm-0558 Attack Analysis
I meant to post this earlier but got distracted by a few other things. Yay for busy life, right?
Earlier this month Microsoft concluded their investigation of the recent Storm-0558 email compromise/attack and the results are... fascinating. I highly recommend checking out the blog post when you get a chance. It's available here. . . .
[SC-100] Sensitive Operations Report Workbook
Just a friendly reminder that the Microsoft sensitive operations report workbook exists and can be super helpful.
For those unfamiliar, it's an Azure Monitor workbook designed to capture activities/events that could be critical or impactful for Azure AD. Examples include:
- Modified application and service . . .
[SC-100] Defender for Cloud - Recommendations vs Alerts vs Vulnerability Assessment
Maybe it's just me, but I was starting to get a little confused on the differences in Azure workload security options. There's essentially three elements:
- "Security Recommendations"
- "Alerts"
- "Vulnerability Assessment"
What's the difference though? Just for the heck . . .
[SC-100] CWPP vs CSPM
Gotta love acronyms and abbreviations, right?
While studying for the SC-100, there's a few terms that kept coming up:
- "Cloud Workload Protection Platform" (CWPP)
- "Cloud Security Posture Management" (CSPM)
I can infer some context based on the names but I was curious to know exactly what the difference was between them. Thankfully, . . .
[SC-100] MCSB Compliance Control Overview
[SC-100] Compliance is not security
I came across this gem in sc-100 prep material:
While compliance provides a consistent required baseline of security best practices and controls, compliance with security standards is insufficient to make an organization "secure". Keeping an organization secure can change dynamically by the week, day, or hour as . . .
[SC-100] Microsoft Entra "Verified ID" Feature Explained
In case I'm not the only person who as a little unfamiliar with Microsoft's "Verified ID" feature, I came across a great video from Andy Malone that walks through a practical example of how it works.
Here's a high-level diagram as well:
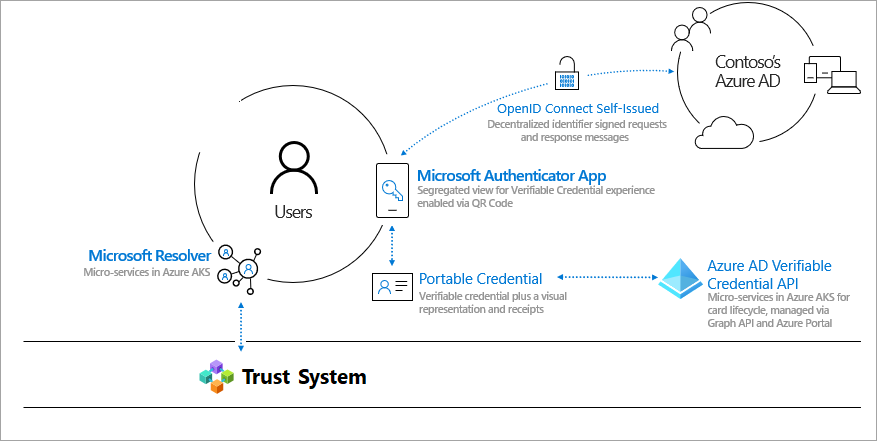
Very interesting and compelling. I think remains to be . . .