[SC-100] Conditional access "what if" tool
More security controls in the market need a feature like this.
I'm digging the "What If" tool in Azure Conditional Access component. The idea is simple: as you're building policies, you can throw various scenarios at the policy engine to understand what the heck it'll do.
This gives admins the opportunity to observe effects and perhaps test variations of authentication use . . .
[SC-100] Sensitive Operations Report Workbook
Just a friendly reminder that the Microsoft sensitive operations report workbook exists and can be super helpful.
For those unfamiliar, it's an Azure Monitor workbook designed to capture activities/events that could be critical or impactful for Azure AD. Examples include:
- Modified application and service . . .
[SC-100] Azure Blueprints vs Azure Landing Zone
This was another topic that was a little confusing: what's the difference between Azure Blueprints and Azure Landing Zone?
I came across various Microsoft documentation but it was still a little... vague.
Here's a nice table, provided courtesy of Google Bard:
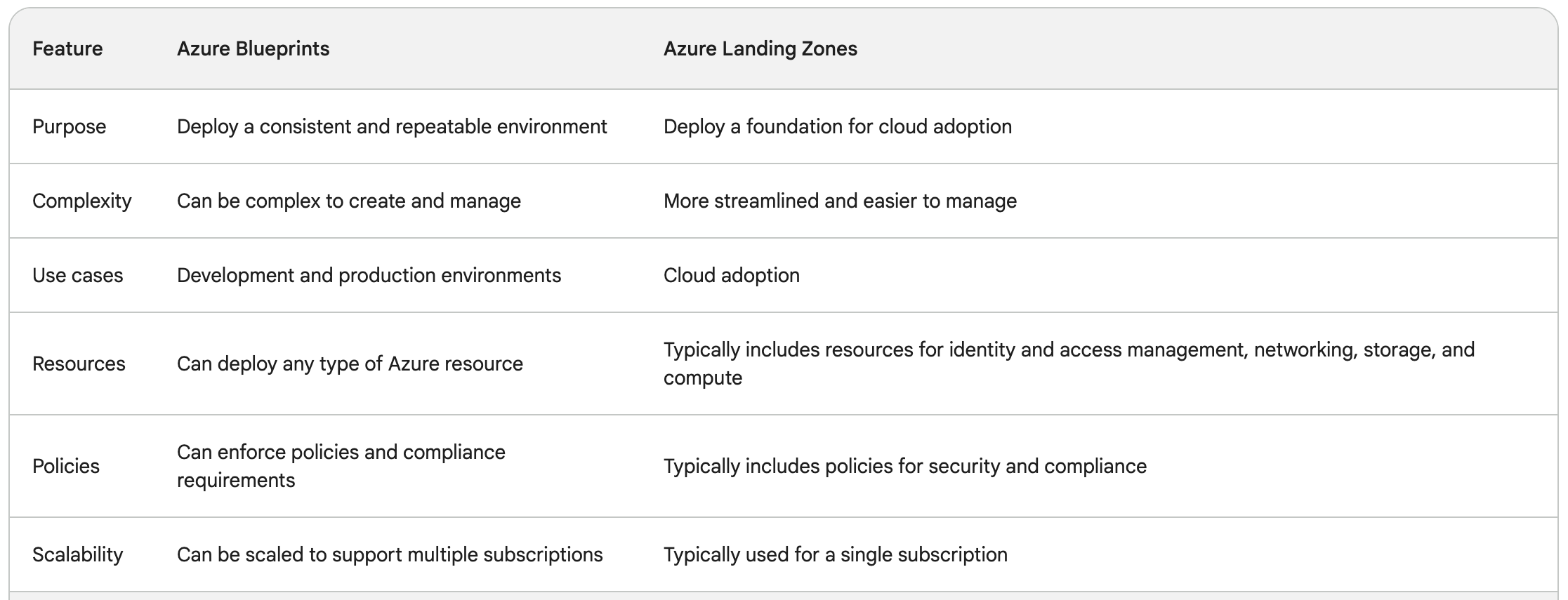
(usual disclaimer about AI-provided . . .
[SC-100] The purpose of Azure Subscriptions
Azure Subscriptions are (to me at least) an interesting concept/term. I've taken several Microsoft exams involving the topic but to date, I haven't necessarily found a succinct way to describe them. This description in SC-100 training documentation is one of the best I've seen:
Everything starts with a subscription, . . .
[SC-100] Defender for Cloud - Recommendations vs Alerts vs Vulnerability Assessment
Maybe it's just me, but I was starting to get a little confused on the differences in Azure workload security options. There's essentially three elements:
- "Security Recommendations"
- "Alerts"
- "Vulnerability Assessment"
What's the difference though? Just for the heck . . .
[SC-100] CWPP vs CSPM
Gotta love acronyms and abbreviations, right?
While studying for the SC-100, there's a few terms that kept coming up:
- "Cloud Workload Protection Platform" (CWPP)
- "Cloud Security Posture Management" (CSPM)
I can infer some context based on the names but I was curious to know exactly what the difference was between them. Thankfully, . . .