[SC-100] Conditional Access frameworks, policies, and naming conventions
OK, OK, so it may not necessarily be the most interesting topic...
Nevertheless, I think this article from Microsoft on Conditional Access framework and policies is an important one.
Of particular note, there's a section on naming conventions and how to develop/establish a system that scales well for designating . . .
[SC-100] The Seven Properties of Highly Secure Devices
Great read from Microsoft: The Seven Properties of Highly Secure Devices.
This doc delves into architectural considerations for designing IoT systems that have security baked in. Good stuff!
[SC-100] Microsoft Entra "Verified ID" Feature Explained
In case I'm not the only person who as a little unfamiliar with Microsoft's "Verified ID" feature, I came across a great video from Andy Malone that walks through a practical example of how it works.
Here's a high-level diagram as well:
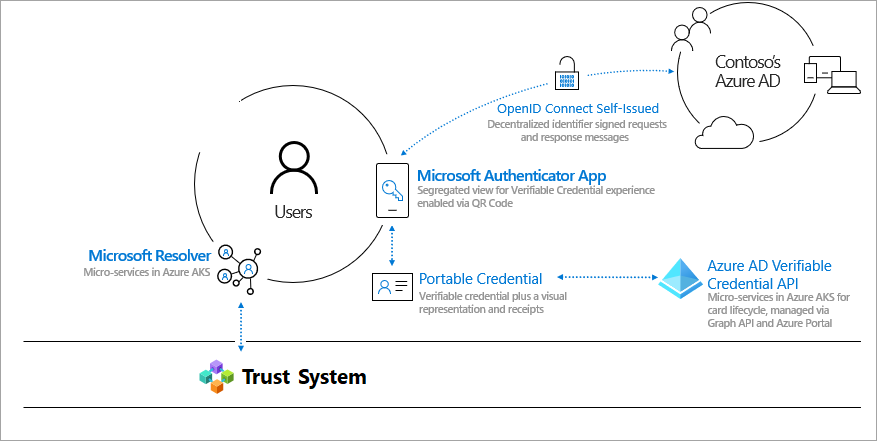
Very interesting and compelling. I think remains to be . . .
[SC-100] Microsoft Graph Refresher
In case I'm not the only person who needed a refresher on Microsoft Graph, here are a few helpful links:
[SC-100] Azure Monitor Agent vs Log Analytics Agent
I came across a nifty article explaining the difference between the legacy Log Analytics Agent and Azure Monitor Agent.
There's some feature improvements in terms of what logs can be retrieved with AMA but I think the biggest notable difference is performance-related. As per Microsoft: "The Azure Monitor agent provides a . . .
[SC-100] Microsoft architectures - the bigger picture
There's a lot of Microsoft diagrams and workflows but this is by far my favorite:
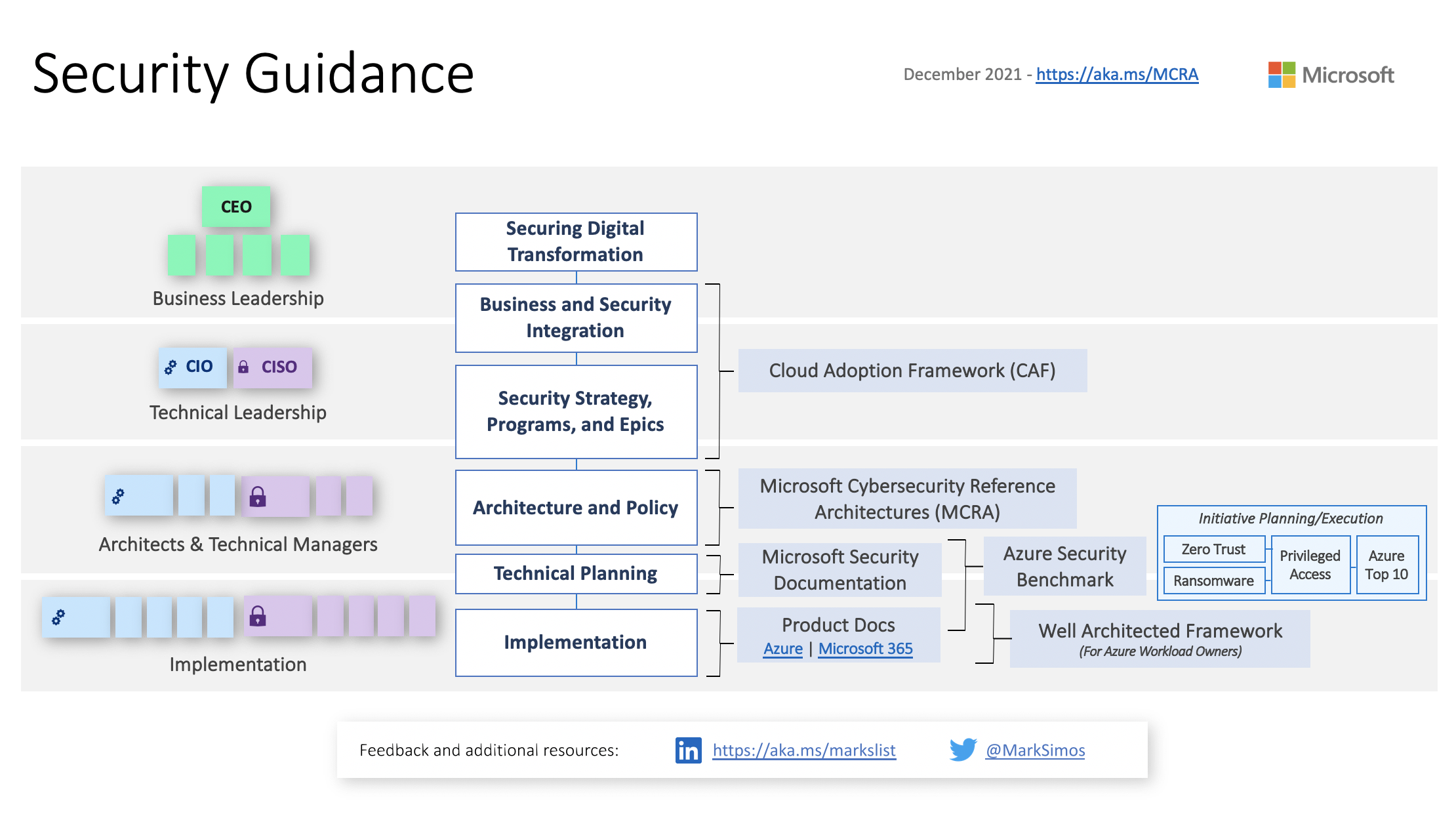
It's a bit dated (2021 feels like a lifetime ago) but the information is still absolutely relevant. This diagram illustrates how different Microsoft reference architectures, models, and resources apply to the various levels of . . .
IoT Architecture Zones
I'm digging this illustration of IoT security architecture zones, courtesy of Microsoft docs.

The beauty of it all is the simple (but effective) principles:
- Segment the solution
- Minimize the impact of lower-trust zones against higher-trust zones
- Assume that as data traverses zones, it could be . . .