[SC-100] Compliance is not security
I came across this gem in sc-100 prep material:
While compliance provides a consistent required baseline of security best practices and controls, compliance with security standards is insufficient to make an organization "secure". Keeping an organization secure can change dynamically by the week, day, or hour as . . .
[SC-100] Conditional Access frameworks, policies, and naming conventions
OK, OK, so it may not necessarily be the most interesting topic...
Nevertheless, I think this article from Microsoft on Conditional Access framework and policies is an important one.
Of particular note, there's a section on naming conventions and how to develop/establish a system that scales well for designating . . .
[SC-100] The Seven Properties of Highly Secure Devices
Great read from Microsoft: The Seven Properties of Highly Secure Devices.
This doc delves into architectural considerations for designing IoT systems that have security baked in. Good stuff!
[SC-100] Identity is more than a username
While studying for the SC-100 exam, a concept really resonated with me: the definition of identity and its purpose in security.
I think for some folks (myself included), it's been all too easy to think of "identity" as a singular credential; a unique data element. Like an ID card. While understandable, I think that . . .
Trivial terminology: MITRE vs MITRE Engenuity?
What's the difference?
I like this succinct explanation from Check Point on the difference between "MITRE" and "MITRE Engenuity". Good stuff.
The MITRE Corporation is a US Government federally funded research and development center (FFRDC), and the MITRE Engenuity is a foundation dedicated to using the research and technology . . .
[SC-100] NIST 800-61 response management phases
I'm digging this simple (but functional!) illustration of the NIST 800-161 response management phases, courtesy of Microsoft Learning:
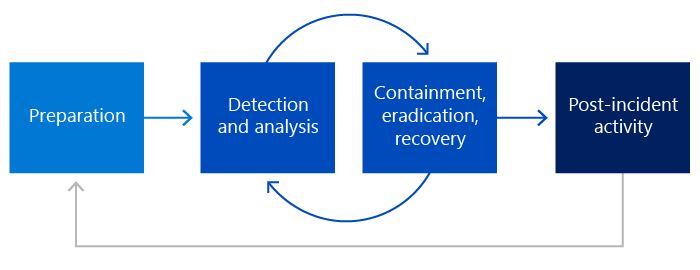
Good stuff!
[SC-100] Simplified explanation of technical response to incidents
While perusing a study guide for SC-100 exam, I came across a really nice and succinct explanation for technical response. It's one of my favorite quotes now:
(...) there are two key goals that every incident response should aim to address from a technical perspective. The first is identifying the scope of the attack (...) . . .