[SC-100] Simplified explanation of technical response to incidents
While perusing a study guide for SC-100 exam, I came across a really nice and succinct explanation for technical response. It's one of my favorite quotes now:
(...) there are two key goals that every incident response should aim to address from a technical perspective. The first is identifying the scope of the attack (...) . . .
Cybersecurity and productivity
I came across a nifty quote by Pete Zerger while watching one of his LinkedIn Learning courses. This one really resonated with me:
Focus on security and productivity. Ensure that security enables productivity as well as reducing risk. If it hampers productivity or increases risk, reconsider.
I know at first . . .
IoT Architecture Zones
I'm digging this illustration of IoT security architecture zones, courtesy of Microsoft docs.

The beauty of it all is the simple (but effective) principles:
- Segment the solution
- Minimize the impact of lower-trust zones against higher-trust zones
- Assume that as data traverses zones, it could be . . .
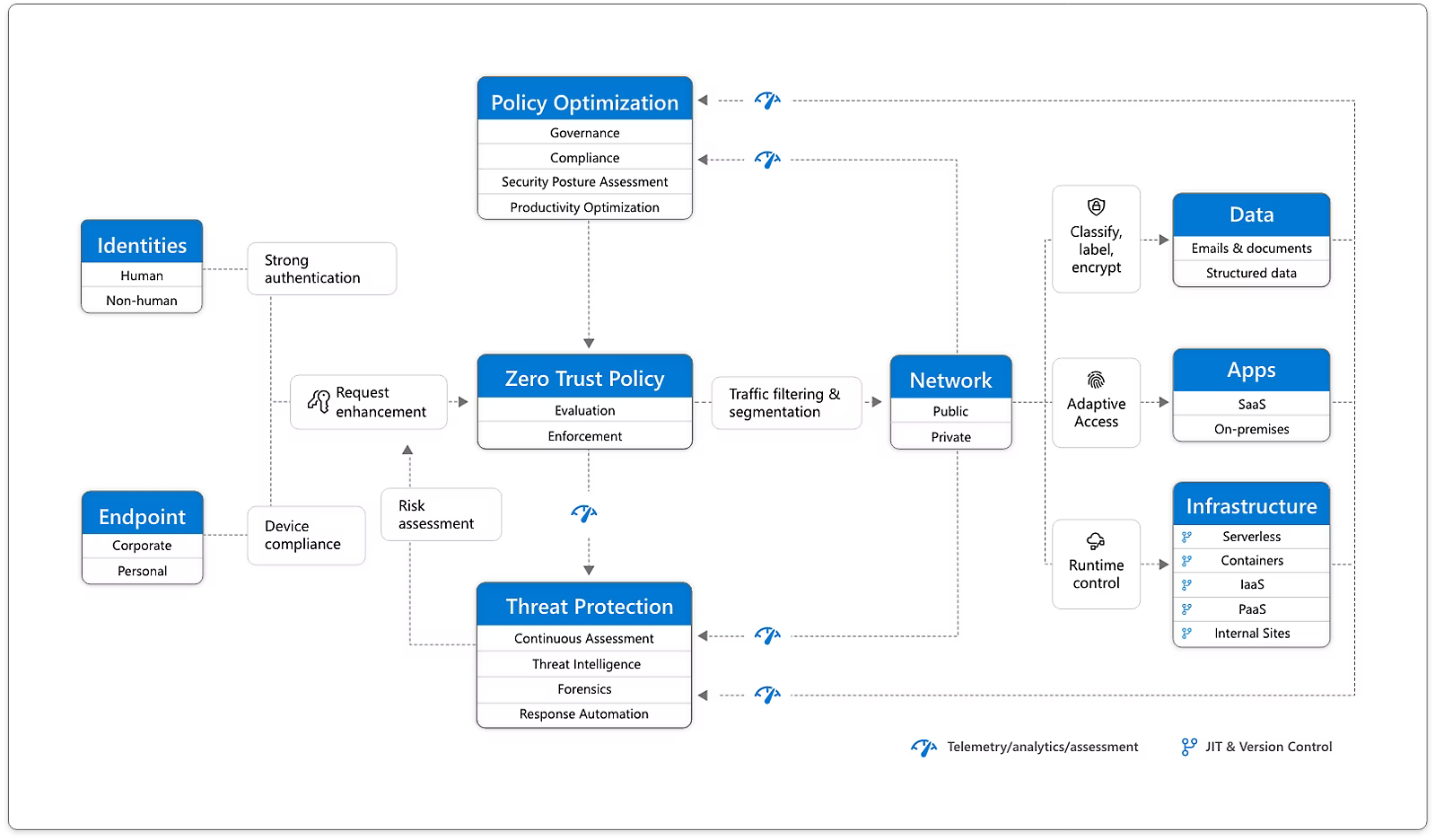
[SC-100 Exam Prep] Zero trust example workflow topology
A (zero trust) picture is worth a thousand words :-)
In preparing for the Microsoft SC-100 exam, I came across a nifty article from Microsoft regarding their position on Zero Trust.
Among other things, it includes a high-level example diagram of a topology combining a number of concepts.
Check it out: