[SC-100] Microsoft architectures - the bigger picture
There's a lot of Microsoft diagrams and workflows but this is by far my favorite:
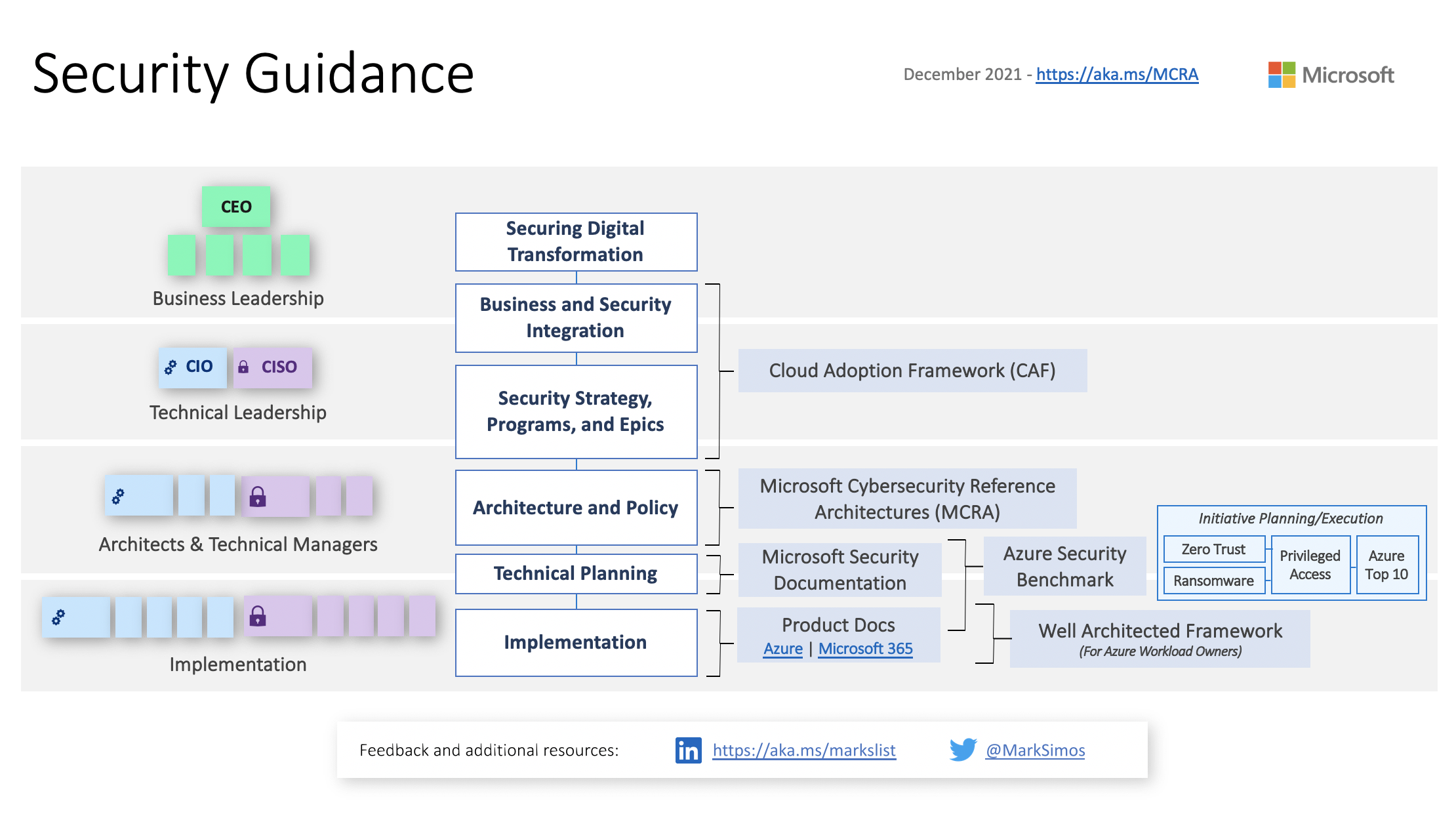
It's a bit dated (2021 feels like a lifetime ago) but the information is still absolutely relevant. This diagram illustrates how different Microsoft reference architectures, models, and resources apply to the various levels of . . .
[Sc-100] Technical Video Overview of MCRA
Because sometimes a video is worth a thousand slides.
In preparing for the SC-100 Microsoft exam, one frequently referenced resource I've come across is the Microsoft Cybersecurity Reference Architecture (MCRA). It's an absolutely brilliant set of concepts, architectures, diagrams, and workflows but there's just one issue: It's a bit of information overload.
I recently . . .
Cybersecurity and productivity
I came across a nifty quote by Pete Zerger while watching one of his LinkedIn Learning courses. This one really resonated with me:
Focus on security and productivity. Ensure that security enables productivity as well as reducing risk. If it hampers productivity or increases risk, reconsider.
I know at first . . .
Initial thoughts on Ubuntu Budgie
This could be my favorite linux distro yet.
This weekend, the fam and I were doing some cleaning and I came across an old relic from a bygone era: my 2008 MacBook.

Remember when these came out? The aluminum frame was new and all the rage.
I loved this thing, and ya know what? I have to give Apple credit: despite being over 15 years old it's held up . . .
IoT Architecture Zones
I'm digging this illustration of IoT security architecture zones, courtesy of Microsoft docs.

The beauty of it all is the simple (but effective) principles:
- Segment the solution
- Minimize the impact of lower-trust zones against higher-trust zones
- Assume that as data traverses zones, it could be . . .
My productivity bookshelf
Every now and then, folks ask me for book recommendations related to productivity. It's a great question, but something that's surprisingly difficult for me to answer. Why? Because everyone has different preferences, styles, and workflows. So what resonates with me won't necessarily work for someone else.
That said, if I . . .
Edgevolt.com -> MikeBerggren.com
What the heck? Why did I get redirected to this blog?
As I mentioned in a prior blog post, I've begun transitioning to a newer blogging platform that's (hopefully) a little easier to maintain. Part of that effort includes consolidating other projects/sites of mine (like Edgevolt Labs).
So, what the heck does this actually mean? Moving forward, future updates for various . . .