[SC-100] NIST 800-61 response management phases
I'm digging this simple (but functional!) illustration of the NIST 800-161 response management phases, courtesy of Microsoft Learning:
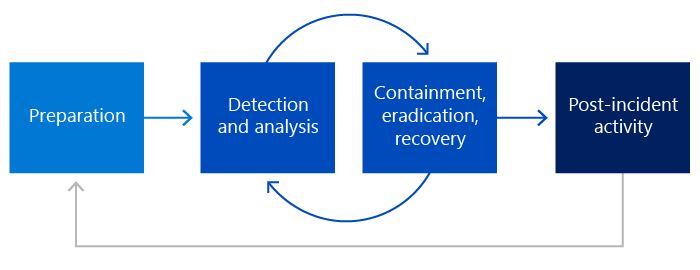
Good stuff!
[SC-100] Simplified explanation of technical response to incidents
While perusing a study guide for SC-100 exam, I came across a really nice and succinct explanation for technical response. It's one of my favorite quotes now:
(...) there are two key goals that every incident response should aim to address from a technical perspective. The first is identifying the scope of the attack (...) . . .
[SC-100] Azure Monitor Agent vs Log Analytics Agent
I came across a nifty article explaining the difference between the legacy Log Analytics Agent and Azure Monitor Agent.
There's some feature improvements in terms of what logs can be retrieved with AMA but I think the biggest notable difference is performance-related. As per Microsoft: "The Azure Monitor agent provides a . . .
Why does curl think my downloaded data is binary?
Because it is.
While working on a project recently, I came across an odd warning upon running curl:
foouser@foo:~$ curl "https://api.foo.example/blah"
Warning: Binary output can mess up your terminal. Use "--output -" to tell
Warning: curl to output it to your terminal anyway, or consider "--output
Warning: . . .[SC-100] Microsoft architectures - the bigger picture
There's a lot of Microsoft diagrams and workflows but this is by far my favorite:
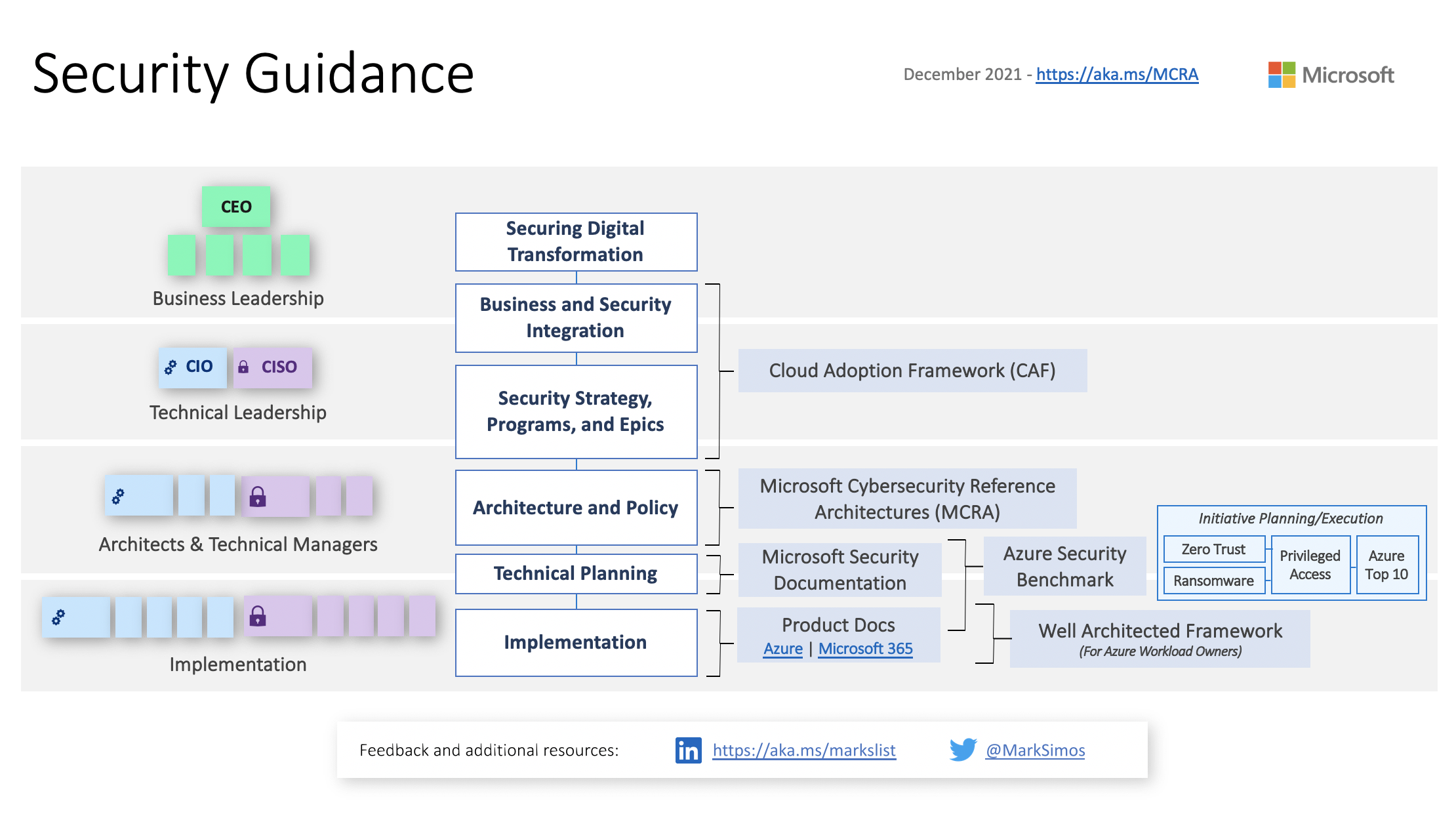
It's a bit dated (2021 feels like a lifetime ago) but the information is still absolutely relevant. This diagram illustrates how different Microsoft reference architectures, models, and resources apply to the various levels of . . .
[Sc-100] Technical Video Overview of MCRA
Because sometimes a video is worth a thousand slides.
In preparing for the SC-100 Microsoft exam, one frequently referenced resource I've come across is the Microsoft Cybersecurity Reference Architecture (MCRA). It's an absolutely brilliant set of concepts, architectures, diagrams, and workflows but there's just one issue: It's a bit of information overload.
I recently . . .
Cybersecurity and productivity
I came across a nifty quote by Pete Zerger while watching one of his LinkedIn Learning courses. This one really resonated with me:
Focus on security and productivity. Ensure that security enables productivity as well as reducing risk. If it hampers productivity or increases risk, reconsider.
I know at first . . .