[SC-100] Azure Blueprints vs Azure Landing Zone
This was another topic that was a little confusing: what's the difference between Azure Blueprints and Azure Landing Zone?
I came across various Microsoft documentation but it was still a little... vague.
Here's a nice table, provided courtesy of Google Bard:
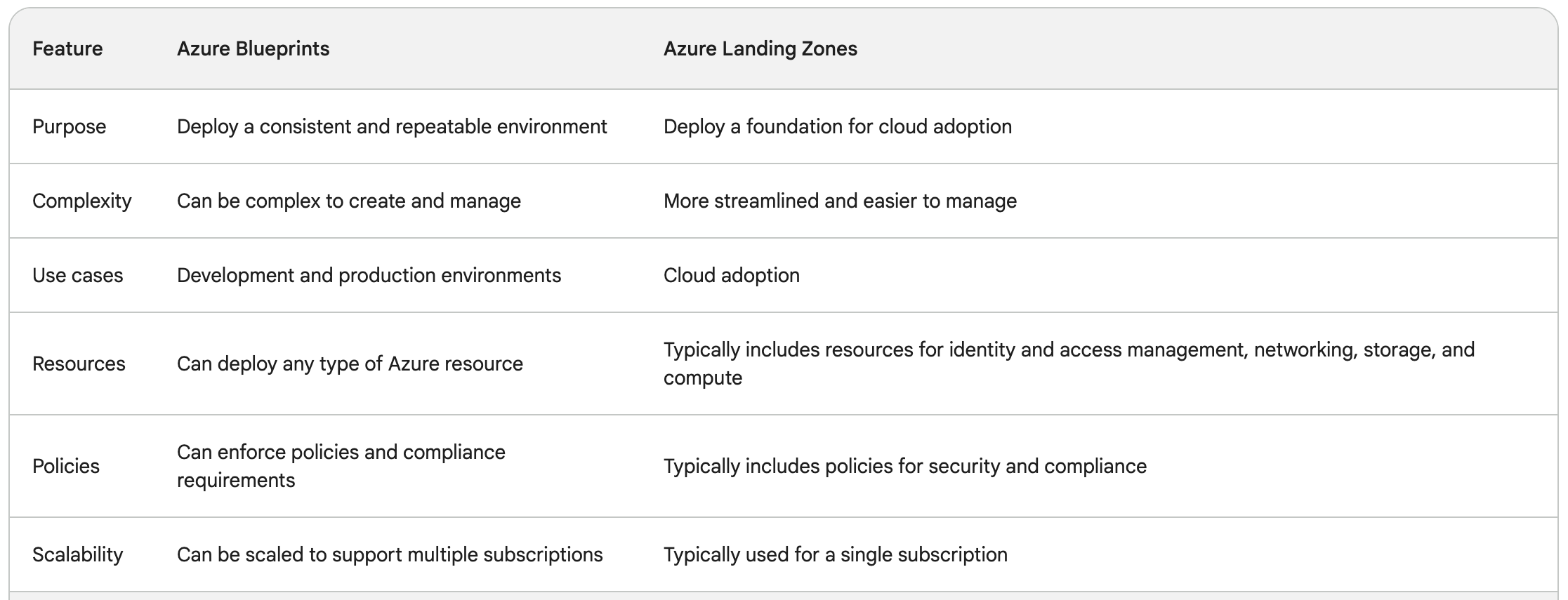
(usual disclaimer about AI-provided . . .
[SC-100] The purpose of Azure Subscriptions
Azure Subscriptions are (to me at least) an interesting concept/term. I've taken several Microsoft exams involving the topic but to date, I haven't necessarily found a succinct way to describe them. This description in SC-100 training documentation is one of the best I've seen:
Everything starts with a subscription, . . .
[SC-100] Defender for Cloud - Recommendations vs Alerts vs Vulnerability Assessment
Maybe it's just me, but I was starting to get a little confused on the differences in Azure workload security options. There's essentially three elements:
- "Security Recommendations"
- "Alerts"
- "Vulnerability Assessment"
What's the difference though? Just for the heck . . .
[SC-100] CWPP vs CSPM
Gotta love acronyms and abbreviations, right?
While studying for the SC-100, there's a few terms that kept coming up:
- "Cloud Workload Protection Platform" (CWPP)
- "Cloud Security Posture Management" (CSPM)
I can infer some context based on the names but I was curious to know exactly what the difference was between them. Thankfully, . . .
[SC-100] MCSB Compliance Control Overview
[SC-100] Security and agility
Another gem from SC-100 study material. Admittedly a little obvious but the thought is expressed very well.
Security needs to become more agile because businesses, government agencies, and other organizations today face a world where services are expected to be provided whenever and wherever people want them.
(Source: . . .
[SC-100] Compliance is not security
I came across this gem in sc-100 prep material:
While compliance provides a consistent required baseline of security best practices and controls, compliance with security standards is insufficient to make an organization "secure". Keeping an organization secure can change dynamically by the week, day, or hour as . . .